Have you ever noticed how Cloud Security System will protect your data?
Cloud security provides you protection for flight data to be stored online and against leakage and deletion. Methods to ensure cloud security include the firewall, penetration testing, obfuscation, tokens, virtual private networks (VPN), and avoiding the public Internet connections. According to Techunido the cloud security, also referred to as cloud computing security consists of a group of policies to control along with some procedures and technologies that work together to protect cloud-based systems, information, and infrastructure.

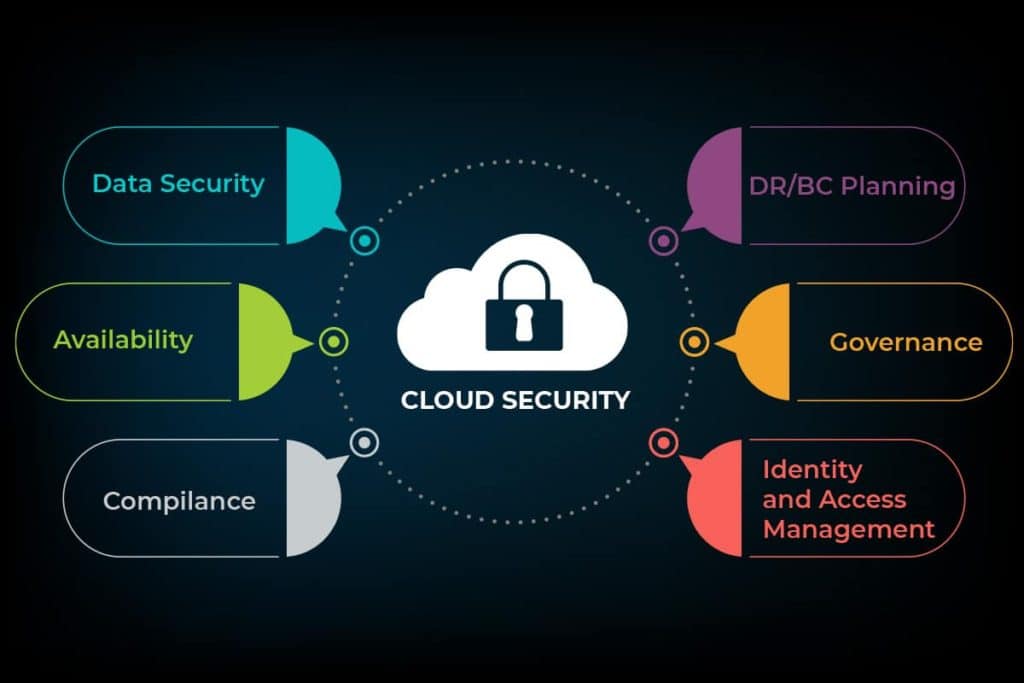
Configurable security measures to safeguard information, support regulatory compliance and safeguard client privacy and authentication set rules for individual users and devices. By authenticating access to traffic filtering, cloud security will be designed to the exact desires of the business. Since these rules can be configured and managed in one place, the result is reduced administrative overhead and data technology groups are authorized to target different areas of the business.
Threats to cloud security
The main threats to cloud security embrace info breaches beside information loss or account hacking and hi-jacking. alternative threats embrace the movement of services, program interface untrusted application (API), dangerous choice of cloud storage suppliers, and sharing that kind of technology that compromises the cloud computing security. Distributed denials of service (DDoS) attacks are another form of threat to cloud security. These kinds of attacks will shut an inculpative data service because users not having the ability to access their information like email or bank accounts.

Cloud security is important for many users who are concerned about the security of the data they store in the cloud. Additionally, data privacy and security are critical for every company and being able to use cloud services without any worry is a benefit. Companies using cloud sometimes believe that their data is safer on their own local server where they believe they have more control over the data.
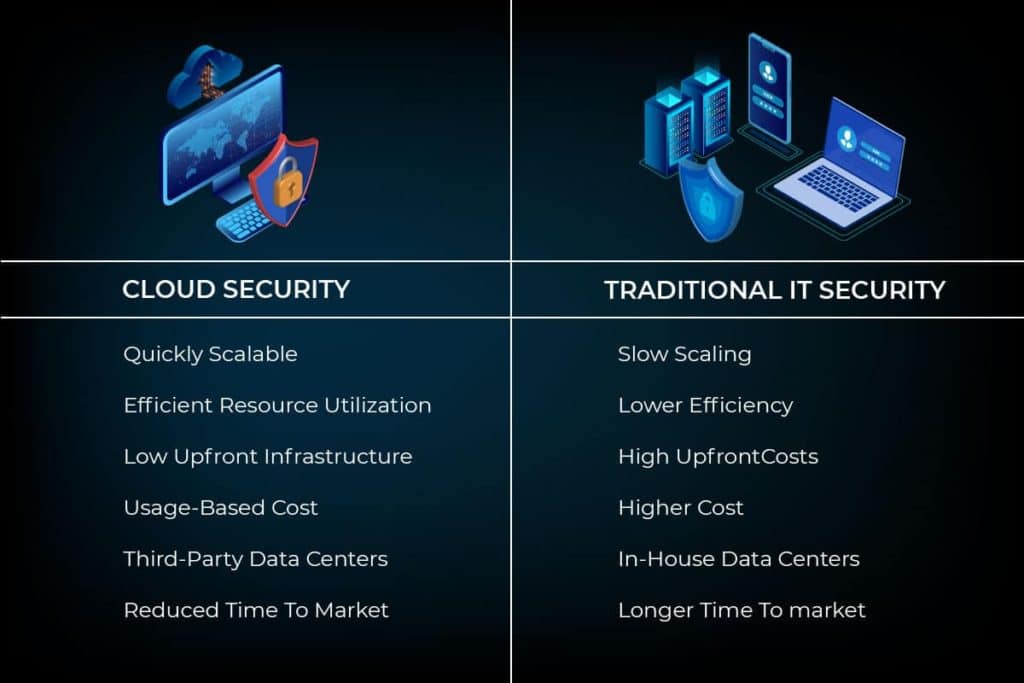
However, data stored in the cloud may be more secure due to cloud service providers having superior safety measures and security experts on staff. The reality is that some hackers try to steal the data from any server or cloud storage, and on-premise data can oftentimes be more vulnerable to security breaches depending on the type of attack. Social engineering and malware can also make data storage systems vulnerable.

Cloud security is a major concern for cloud storage providers and users too. Not only do they have to satisfy their customers, but they also have to follow important regulatory requirements for storing sensitive data such as credit card numbers and health information. Third-party audits for cloud security systems and procedures are ultimately the best approach to ensuring that user data remains secure.

